WHAT'S YOUR CYBERSECURITY MATURITY ?

What's you Cybersecurity Maturity?:
Check the NIST Cybersecurity Framework, CIS Controls or ISO 2700.
In today's digital age, cybersecurity is a critical concern for organisations of all sizes and industries. With the increasing frequency and sophistication of cyber threats, it's imperative for organisations to assess and improve their cybersecurity posture continually. One effective way to do this is by measuring their cybersecurity maturity. Cybersecurity maturity assessments provide insights into an organisation's ability to protect its digital assets and sensitive information. In this article, we will explore the steps to determine the cybersecurity maturity of an organisation.
What is Cybersecurity Maturity?
Cybersecurity maturity refers to an organisation's level of preparedness and capability to defend against cyber threats. It is not a one-size-fits-all concept, as organisations have different needs and risks. Maturity assessments help organisations identify their current cybersecurity state and establish a roadmap for improvement.
Steps to Determine Cybersecurity Maturity:
- Define Objectives and Scope:
Before conducting a cybersecurity maturity assessment, it's crucial to define clear objectives and the scope of the assessment. Determine what aspects of your organisation's cybersecurity you want to evaluate, such as network security, data protection, incident response, and employee training.
- Choose a Maturity Model:
Several cybersecurity maturity models are available, such as the NIST Cybersecurity Framework, CIS Controls, and ISO 27001 (see below). Choose a model that aligns with your organisation's goals, regulatory requirements, and industry best practices. These frameworks provide a structured approach to assessing and improving cybersecurity maturity.
- Conduct a Baseline Assessment:
Start by assessing your organisation's current cybersecurity posture. This involves gathering data on your security policies, procedures, technologies, and practices. You can use questionnaires, interviews, and automated tools to collect information. This baseline assessment helps establish a starting point for measuring progress.
- Evaluate Your Current State:
Using the chosen maturity model, assess your organisations current cybersecurity maturity level. Maturity levels are typically divided into stages, such as "initial," "repeatable," "defined," "managed," and "optimised." Assess where your organisation falls within these stages for each aspect of cybersecurity.
- Identify Gaps:
Compare your current maturity levels with the desired maturity levels outlined in the chosen maturity model. This step helps identify gaps in your cybersecurity practices. These gaps represent areas where improvements are needed to enhance your cybersecurity maturity.
- Prioritize Improvements:
Not all cybersecurity weaknesses are equally critical. Prioritise the identified gaps based on their potential impact and risk to your organisation. Consider factors like the likelihood of an attack and the potential consequences of a successful breach.
- Develop a Roadmap:
Create a cybersecurity improvement roadmap that outlines the steps, resources, and timelines required to address the identified gaps. Ensure that your roadmap aligns with your organisation's budget and strategic goals.
- Implement Changes:
Start implementing the changes and improvements outlined in your roadmap. This may involve deploying new security technologies, updating policies and procedures, providing training to employees, and enhancing incident response capabilities.
- Monitor and Measure:
Regularly monitor your organisation's cybersecurity maturity using the same framework or model you used for the initial assessment. This allows you to track progress over time and identify new gaps or emerging threats.
- Continuous Improvement:
Cybersecurity is an ongoing process. Continuously review and update your cybersecurity practices to adapt to evolving threats and technologies. Regularly reassess your maturity level to ensure that you are maintaining or increasing your cybersecurity resilience.
Conclusion
Determining the cybersecurity maturity of an organisation is a crucial step in safeguarding digital assets and sensitive information. It provides a structured approach to assessing and improving cybersecurity practices. By following these steps and committing to continuous improvement, organisations can enhance their cybersecurity posture and better protect themselves from cyber threats. Remember that cybersecurity is not a one-time effort but an ongoing commitment to staying ahead of evolving threats in the digital landscape.
The NIST Cybersecurity Framework, CIS Controls, and ISO 27001
These are widely recognized frameworks that provide a structured approach to managing and improving cybersecurity, but they have different focuses and applications.
-
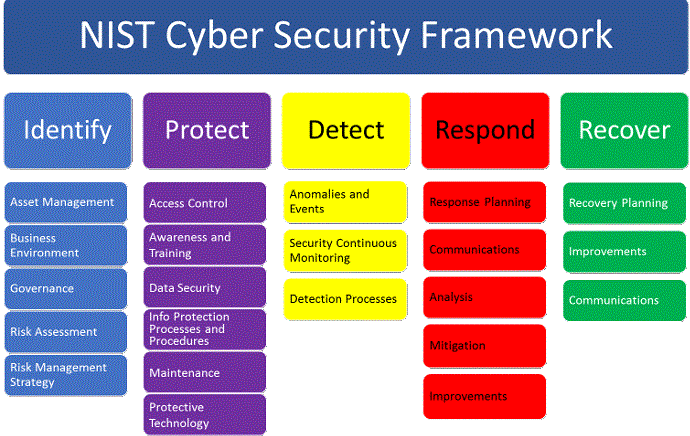
NIST Cybersecurity Framework:
-
Definition: The National Institute of Standards and Technology (NIST) Cybersecurity Framework is a set of guidelines, best practices, and standards developed by the U.S. government to help organisations manage and mitigate cybersecurity risks. It was created in response to Executive Order 13636, which aimed to improve critical infrastructure cybersecurity.
-
The NIST framework consists of five core functions:
- Identify: Understand and manage cybersecurity risks.
- Protect: Implement safeguards to protect against cyber threats.
- Detect: Develop capabilities to identify cybersecurity incidents.
- Respond: Establish an effective incident response and recovery plan.
- Recover: Ensure the organization's ability to recover from a cybersecurity incident.
-
Categories and Subcategories: Each core function is divided into categories and further into subcategories, providing specific guidance on cybersecurity controls and practices.
-
Usage: The NIST Cybersecurity Framework is widely adopted by organizations, especially in the United States, as a flexible and adaptable framework to improve their cybersecurity posture.
-
-
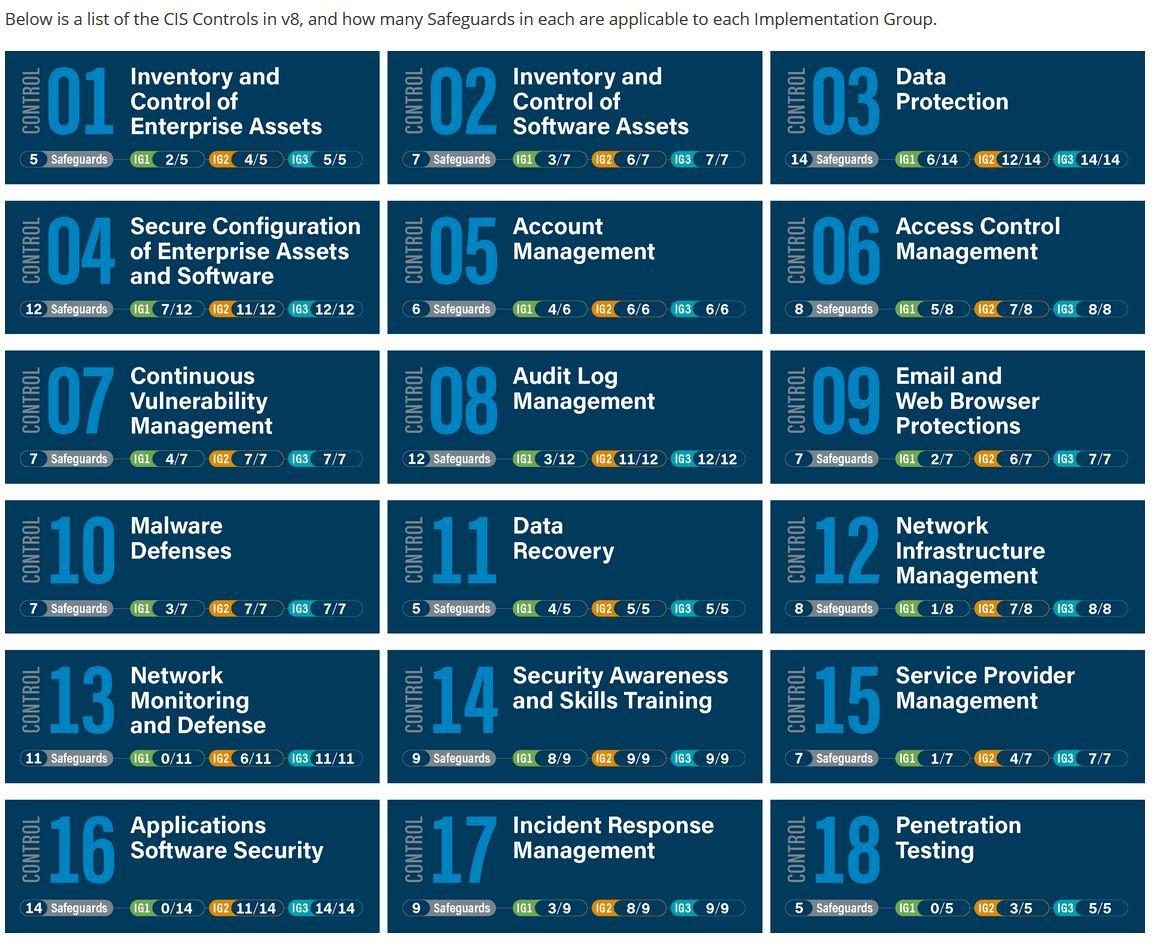
CIS Controls (Center for Internet Security Controls):
-
Definition: The CIS Controls, developed by the Center for Internet Security (CIS), are a set of best practices and guidelines designed to help organizations bolster their cybersecurity defenses. These controls are prioritized based on their effectiveness in reducing the risk of cyberattacks.
-
Components:
-
20 Critical Controls: The CIS Controls consist of 20 high-priority actions that organizations should implement to enhance their cybersecurity posture. These controls are organized into three categories:
- Basic: Controls 1-6
- Foundational: Controls 7-16
- Organizational: Controls 17-20
-
Implementation Groups (IGs): The controls are divided into three implementation groups, each tailored to different organizational sizes and maturity levels.
-
-
Usage: CIS Controls are widely adopted by organizations looking for practical, actionable steps to improve cybersecurity. They are often used as a prioritized roadmap for implementing security measures.
-
.jpg?width=825&height=450&name=ISO%2027001_Artikel(1).jpg)
-
ISO 27001 (International Organization for Standardization):
-
Definition: ISO 27001 is an internationally recognized standard for Information Security Management Systems (ISMS). It provides a systematic and comprehensive approach to managing information security risks and protecting sensitive data.
-
Components:
-
Risk Management: ISO 27001 places a strong emphasis on risk assessment and management. Organizations must identify, assess, and mitigate information security risks.
-
Control Objectives and Controls: ISO 27001 specifies control objectives and controls across 14 domains, including information security policies, asset management, access control, and incident management. These controls are designed to mitigate identified risks.
-
PDCA Cycle: ISO 27001 follows the Plan-Do-Check-Act (PDCA) cycle, promoting continuous improvement in an organization's information security management system.
-
-
Usage: ISO 27001 certification is pursued by organizations that want to demonstrate their commitment to information security and gain a competitive edge. It's often used in industries where data security and privacy are critical, such as healthcare, finance, and government.
-
In summary, these frameworks and standards serve as valuable tools to enhance an organisation's cybersecurity posture. While NIST provides a flexible framework with core functions, CIS Controls offer a prioritised list of actionable controls, and ISO 27001 is a comprehensive standard for building and maintaining an Information Security Management System. The choice between them depends on an organisation's specific needs, regulatory requirements, and industry best practices.


