HOW TO RESPOND TO RANSOMWARE
This article is based on an online round table "How to respond to ransomware attacks” organised by Pointury on September 22, 2022, during which a group of digital leaders met to discuss cyberthreats with Miguel De Bruycker, Managing Director of the Centre for Cyber security Belgium.

The mission of the Centre for Cyber security Belgium (CCB)
We spend more than 30% of our lives in an anonymous cyberspace. Would you still take a plane, if passengers can take a flight anonymously? Would you drive, if drivers can drive anonymously? The internet has lead to prosperity, yet it requires trust in the environment. That means cybersecurity. People believe that they are secure in cyberspace, which is not the reality. There is no policy. There are no cameras.
Zero trust is too hard to implement. The impact on users would be too significant. So, we want to decrease vulnerability while maintaining an open, free and anonymous cyberspace. That requires extra layers of liability and accountability.
The mission of the CCB is to make Belgium one of the least vulnerable countries. Its strategy is called "active cyber protection". At this moment Belgium is a front runner in cyber security in Europe.
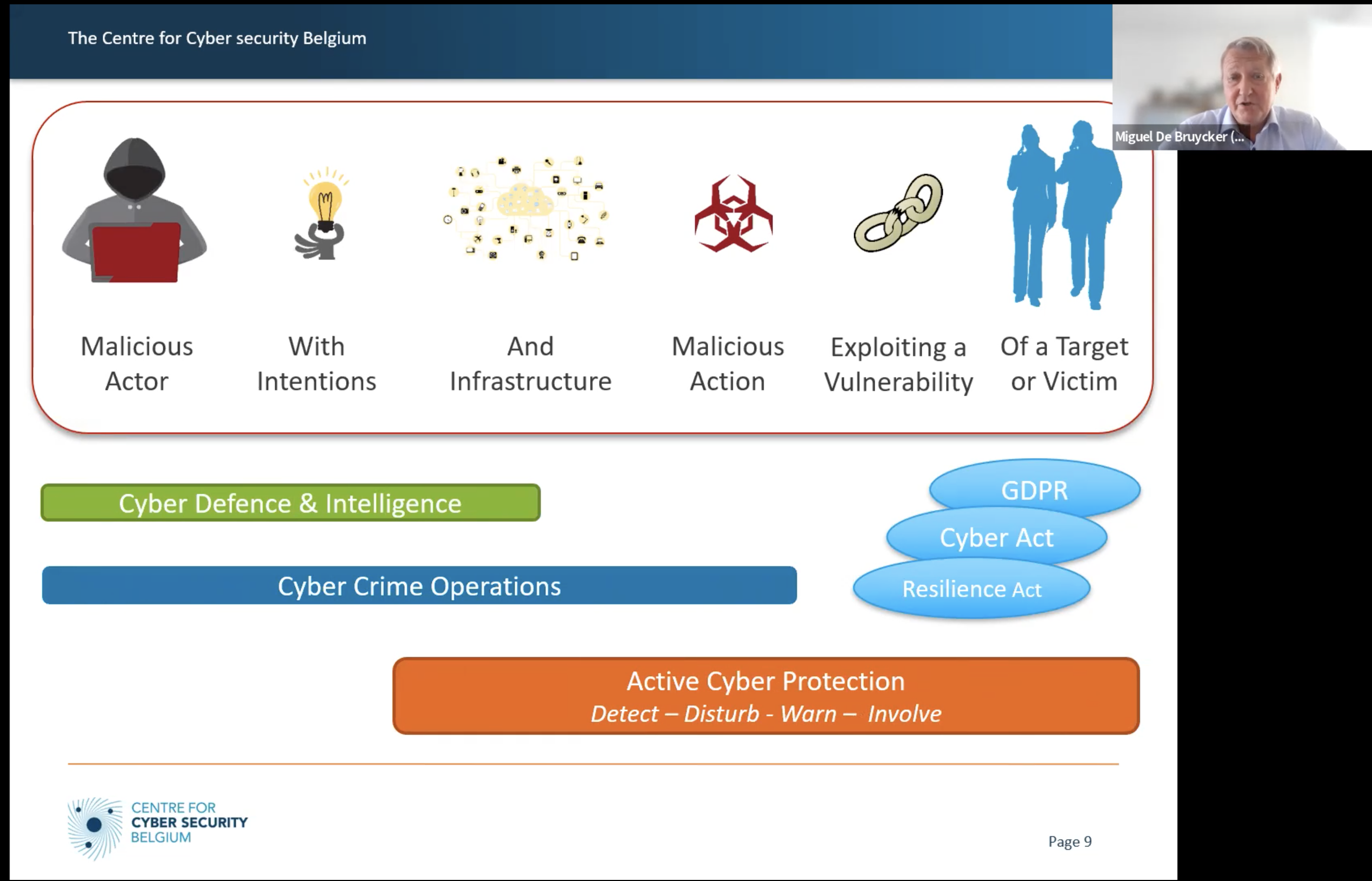
The way in which organisations typically get victimised is the following.
- Detecting vulnerabilities.
- Hackers are constantly looking for new vulnerabilities. These may result from misconfigurations, shadow IT, malware or people not recognising phishing. If they find the vulnerabilities, they may end up on lists on the dark web. That's the starting point. Your organisation, its size, wealth or reputation is typically not the starting point. Only detected vulnerabilities are.
- Exploiting vulnerabilities
- The same group or another group will make use of it. That is called "privilege escalation". It is the act of exploiting a bug, a design flaw, or a configuration oversight in an operating system or software application to gain elevated access to resources that are normally protected from an application or user. The result is that an application with more privileges than intended by the application developer or system administrator can perform unauthorised actions.
- Network reconnaissance & lateral movement
- Network reconnaissance is a term for testing for potential vulnerabilities in a computer network. This may be a legitimate activity by the network owner/operator, seeking to protect it or to enforce its acceptable use policy. It also may be a precursor to external attacks on the network.
- Lateral movement is the process by which attackers spread from an entry point to the rest of the network. There are many methods by which they can achieve this. For instance, an attack could start with malware on an employee's desktop computer. From there, the attacker attempts to move laterally to infect other computers on the network, to infect internal servers, and so on until they reach their final target.
- Network reconnaissance is a term for testing for potential vulnerabilities in a computer network. This may be a legitimate activity by the network owner/operator, seeking to protect it or to enforce its acceptable use policy. It also may be a precursor to external attacks on the network.
- Data exfiltration
- Data exfiltration occurs when malware and/or a malicious actor carries out an unauthorised data transfer from a computer. It is also commonly called data extrusion or data exportation. Data exfiltration is also considered a form of data theft. Since the year 2000, a number of data exfiltration efforts severely damaged the consumer confidence, corporate valuation, and intellectual property of businesses and national security of governments across the world.
- It is a technique to put extra pressure on the victim. The criminals not only ask money for decrypting the data but also blackmail the victim that they would confront their customers with the stolen data.
- Encryption
- Ransomware uses asymmetric encryption. This is cryptography that uses a pair of keys to encrypt and decrypt a file. The public-private pair of keys is uniquely generated by the attacker for the victim, with the private key to decrypt the files stored on the attacker's server.
- Ransom negotiation
- It requires securing the best possible deal and ensuring a successful outcome from criminals you cannot fully trust.
**********************
Overview of protective measures to take.
- 2 Factor Authentication
- Two-factor authentication (2FA) protects against phishing, social engineering and password brute-force attacks and secures your logins from attackers exploiting weak or stolen credentials.
- 2FA becomes more necessary as people now typically work from various places.
- Regular system updates and patches
- Patches are software and operating system (OS) updates that address security vulnerabilities within a program or product. Software vendors may choose to release updates to fix performance bugs, as well as to provide enhanced security features.
- Remote Desktop Protocol (RDP) protection
- Remote desktop protocol (RDP) is a secure network communications protocol developed by Microsoft. It enables network administrators to remotely diagnose problems that individual users encounter and gives users remote access to their physical work desktop computers.
- User awareness training
- User security awareness, typically a component of a company’s security policy, includes educating and testing employees to help protect your business against cybercrimes, including phishing and other social-engineering attacks.
- It is similar with traffic. Even if you have the safest car in the world, if you drive like a fool, you will not be safe.
- The CCB gets on average 15.000 messages per day notifying of suspicious emails. This gives quite a good view of phishing campaigns. It allowed the CCB e.g. to catch a group in Antwerp beginning of this year. Phishing campaigns come more and more from within our country, more and more sophisticated and harder to recognise.
- Regular backups, stored offline.
- A cold backup, also called an offline backup, is a database backup during which the database is offline and not accessible to update. This is the safest way to back up because it avoids the risk of copying data that may be in the process of being updated.
- The backups need to be stored disconnected from the network to prevent them to become infected.
- Security operation center (SOC) and monitoring
- Security Operation Center (SOC) is a centralised function within an organisation employing people, processes, and technology to continuously monitor and improve an organisation's security posture while preventing, detecting, analysing, and responding to cybersecurity incidents.
- Privileged access management (PAM)
- In an enterprise environment, “privileged access” is a term used to designate special access or abilities above and beyond that of a standard user. Privileged access allows organisations to secure their infrastructure and applications, run business efficiently and maintain the confidentiality of sensitive data and critical infrastructure.
- Endpoint anti-ransomware protection
- Endpoint security protects end-user devices through a process that leverages threat intelligence to detect, block, and remediate cybersecurity threats in your network
- Be prepared. Have a plan for when you become a victim.
- A business continuity plan (BCP) is a system of prevention and recovery from potential threats to a company. The plan ensures that personnel and assets are protected and are able to function quickly in the event of a disaster
- A disaster recovery plan (DRP) maps out the process of resuming normal business operations, reconstructing or salvaging vital and other important records and equipment, and becomes a guide for all managers and employees during and after a disaster.
- Business continuity focuses on keeping business operational during a disaster, while disaster recovery focuses on restoring data access and IT infrastructure after a disaster.
**********************
Organisations should assume that sooner or later they will be confronted with a ransomware attack. The main question is when. The CCB is informed of ransomware cases on a weekly basis.
Miguel De Bruycker, Managing Director of the Centre for Cyber security Belgium, has written an article "HOW TO RESPOND TO A RANSOMWARE ATTACK IN 12 STEPS". The article is a guide about urgent actions to take when a ransomware has hit your company.
In summary:
What NOT to do?
- Do not panic. Execute your business continuity plan.
- Do not shut systems down. It's too late anyway and could get things worse.
- Do not search for somebody to blame. Team up.
- Do not pay ransomware. At least, that's the official advise.
The 12 actions are the following.
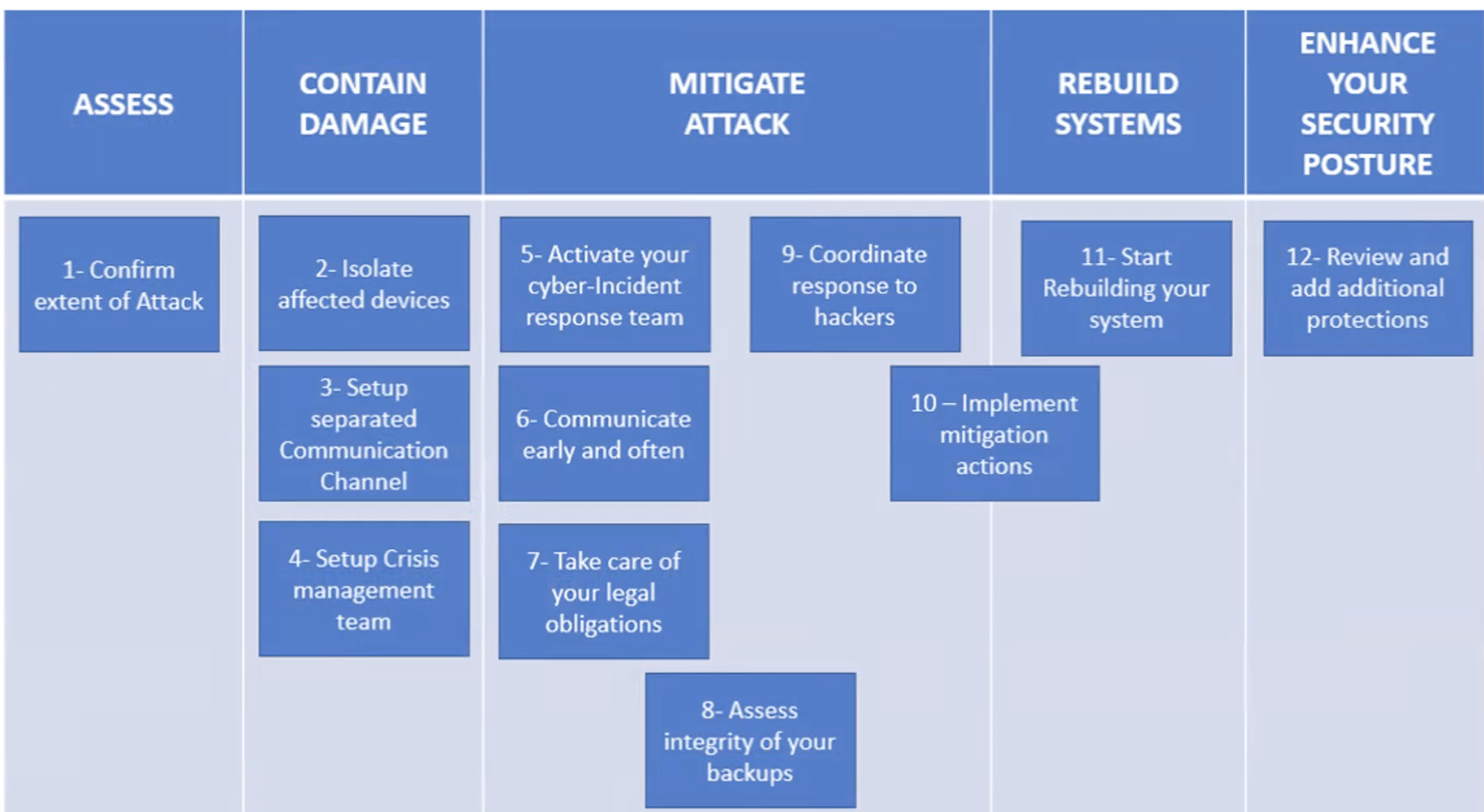
- Determine and confirm the extent of the Ransomware attack
- Isolate affected devices
- Set up a separated communication channel
- Set up a crisis management team
- Activate your cyber incident response team
- Communicate early and often
- Take care of your legal obligations
- Assess the integrity of your backups
- Coordinate your response to the hackers
- Implement mitigation actions
- Start rebuilding your systems
- Review and add additional protections to prevent a future attack
Read the article for details.
**********************
Some questions and answers.
- Is it possible to know if your organisation is listed for certain vulnerabilities on the dark web?
- In a lot of cases you can get the same information as the criminals.
- The CCB has an early warning system in particular for critical organisations. They are also following up known vulnerabilities or detecting new vulnerabilities. The CCB has the legal right to scan for vulnerabilities yet with precaution and with proportionality. With the new data retention law, the CCB will have the right to obtain the contact data of the owner of a vulnerable system from the internet providers. This is what the CCB calls "spear warning" as a reaction to "spear fishing". This should allow organisations to close the vulnerabilities before hackers exploit them.
- Does it make sense to encrypt data on your own systems?
- Encrypting all your data is not easy to do. Not many organisations do that, in particular as it is likely that hackers will first get all the data in active directory and hence get access to the encrypted data anyway.
- Does the CCB share indicators of compromise (IoC)
- During a cybersecurity incident, indicators of compromise (IoC) are clues and evidence of a data breach. These digital breadcrumbs can reveal not just that an attack has occurred, but often, what tools were used in the attack and who's behind them.
- The CCB shares as much IoC information as possible and legally authorised. The CCB collects about 500.00O indicators of compromise (IoC) per month. The amount is enormous and analysing it is a challenge. That is possible for a specific investigation, yet impossible for protection. The focus is on certain sectors such a nuclear and utilities.
- Will zero trust measures become mandatory?
- Zero trust is a wonderful concept. It is not new. It has been around under different names. It is already beyond the hype. It will grow slowly.
- What are you thinking about Bug bounty program versus Pen-testing ?
- A penetration test, colloquially known as a pen test or ethical hacking, is an authorised simulated cyberattack on a computer system, performed to evaluate the security of the system. It is not to be confused with a vulnerability assessment. The test is performed to identify weaknesses (vulnerabilities), including the potential for unauthorised parties to gain access to the system's features and data, as well as strengths, enabling a full risk assessment to be completed.
- A bug bounty program, also called a vulnerability rewards program (VRP), is a crowdsourcing initiative that rewards individuals for discovering and reporting software bugs. Bug bounty programs are often initiated to supplement internal code audits and penetration tests as part of an organisation's vulnerability management strategy.
- You should look to a bug bounty program only when you have a very mature pen-testing program.
- Ideally you do both yet pen-testing first. Pen testing gives you a ‘picture' in time. Applications are often developed daily/weekly. Bounty hunting is a more agile entry to find bugs/exploits.
- It is important to not leave the reports of the pen testing in the boardroom. They need to be brought to the developers.
- What do you think about multi-factor authentication?
- Multi-factor authentication (MFA), encompassing two-factor authentication (2FA), is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence (or factors) to an authentication mechanism such as knowledge (something only the user knows), possession (something only the user has such as a smartphone app), and inherence (something only the user is).
- MFA is also easy to bypass, if the user is not trained on recognising the threats of fishing. 2FA can be bypassed, using the end user himself to approve the 2FA request. Cisco, Twitter, Rockstar & Uber were all victim after MFA being bypassed. Uber was hacked through a Push MFA fatigue.
- Why are so many companies victim of ransomware?
- Everyone has a plan, until they get punched in the face.
- Always assume you are compromised. It helps in getting a process in place to act fast if you are in time to act.
- Where do cybercriminals operate from?
- 75% from Russia, followed by North Korea and China.
- We have seen a big drop in cyberattacks during the first 3 months of the war. Groups of cybercriminals fell apart as a protest against the war. By now they have reorganised and ransomware attacks are again at the levels before the war.
- Do companies spend enough on cybersecurity?
- As with driving, people start slowing down when fined for driving too fast. Companies start spending more on cybersecurity after it went wrong.
- Insurance based companies start asking for a minimum level of cybersecurity. That may help to increase investments.
- What exists to help CISO from different companies to collaborate, in a context where the number of cybersecurity experts is very limited?
- The CCB has an early warning system for a select group of about 10O critical organisations.
- The CCB has quarterly threat report online event with usually more than 1000 participants.
- There are CISO groups on Linkedin to bring cybersecurity expert together.
- Networking events about cybersecurity such as organised by Pointury contribute to CIO's and CISO's to get to know each other.
- Severa vendors offer subscriptions to curated lists of new threats.
**********************
Conclusion.
Ransomware is an important business risk. The risk can be reduced significantly yet will never be zero. So, be ready to respond.
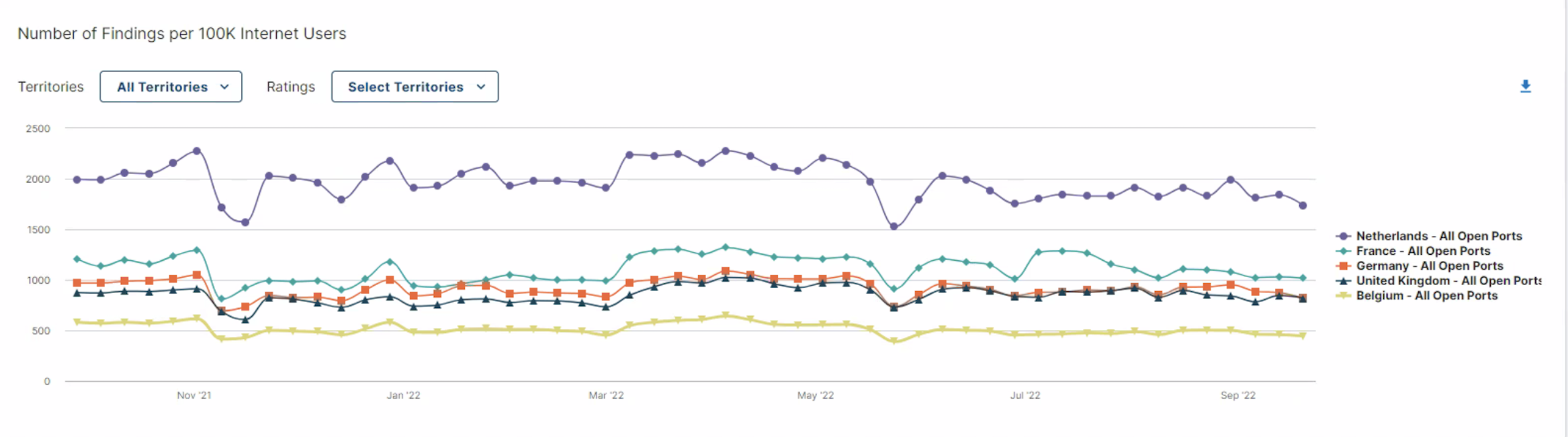
To end on a positive note, Belgium is doing quite well when it comes to number of vulnerabilities and infections per 100k internet users compared to other European countries.
**********************
If you need support with cybersecurity, you could contact
Centre for Cybersecurity Belgium (CCB), the national authority for cybersecurity in Belgium, supervises, coordinates and monitors the application of the Belgian cyber security strategy. Through optimal information exchange, companies, the government, providers of essential services and the population can protect themselves appropriately. The CCB was established by Royal Decree of 10 October 2014 and operates under the authority of the Prime Minister. It is headed by director Miguel de Bruycker and deputy director Phédra Clouner.
Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. With the world’s most distributed compute platform — from cloud to edge — we make it easy for customers to develop and run applications, while we keep experiences closer to users and threats farther away.
- www.akamai.com
- Conti’s Hacker Manuals — Read, Reviewed & Analysed
- Contact: Richard Meeus, Director of Security Technology and Strategy EMEA at Akamai Technologies, rmeeus@akamai.com
CGI is among the largest IT and business consulting services firms in the world. We are insights-driven and outcome-based to help accelerate returns on your IT and business investments. In all we do, our goal is to build trusted relationships through client proximity, providing industry and technology expertise to help you meet the needs of your customers and citizens.
- www.cgi.com
- CGI's cybersecurity offering
- Contact: Tony Chebli, Cybersecurity Senior Consultant at CGI Belux, tony.chebli@cgi.com
Check Point Software Technologies Ltd. is a leading provider of cyber security solutions to governments and corporate enterprises globally. Its solutions protect customers from cyber-attacks with an industry leading catch rate of malware, ransomware and other types of attacks. Check Point offers a multilevel security architecture that defends enterprises’ cloud, network and mobile device held information, plus the most comprehensive and intuitive one point of control security management system. Check Point protects over 100.000 organisations of all sizes.
- www.checkpoint.com
- Check Point's incident response offering
- Article about the Conti ransomware group
- CIS Benchmarks
- Contact: Tom De Laet, Incident Response Team Lead EMEA at Check Point Software Technologies, tdelaet@checkpoint.com
Easi is an all-round IT solutions and service provider that embodies Human Excellence. They want to equip companies with an optimum IT set-up, where they take full responsibility for the security of their infrastructure and software applications.
- www.easi.net
- Easi's cybersecurity offering
- Contact: Quincy Cabral, Account Manager - Partner at EASI, q.cabral@easi.net
F5 Inc. helps thousands of customers across all industries safely and quickly deploy applications in a multi-cloud environment, providing essential building blocks required to make those applications fluidly adapt to each environment. This scalability offers unparalleled flexibility, which better serves the needs of businesses and its customers/end-users and the complex technology stacks.
- www.F5.com
- All F5 Labs content
- Article on How to Pen Test the C-Suite for Cybersecurity Readiness
- Contact: Pieter Slavenburg, Director Sales at BeNeLux F5 Networks, p.slavenburg@f5.com
SentinelOne was founded in 2013 by an elite team of cybersecurity and defence experts who developed a fundamentally new, groundbreaking approach to endpoint protection. SentinelOne is a pioneer in delivering autonomous security for the endpoint, datacenter and cloud environments to help organisations secure their assets with speed and simplicity. SentinelOne unifies prevention, detection, response, remediation and forensics in a single platform powered by artificial intelligence. With SentinelOne, organisations can detect malicious behaviour across multiple vectors, rapidly eliminate threats with fully-automated integrated response and to adapt their defences against the most advanced cyberattacks. SentinelOne has offices in Mountain View, Tel Aviv, and Tokyo. The company is recognized by Gartner in the Endpoint Protection Magic Quadrant as a Leader and has enterprise customers worldwide.
- www.sentinelone.com
- Contact: Andreas Van Nimmen, Commercial Sales at SentinelOne, andreasv@sentinelone.com

.png)
