QUANTUM STEP IN CYBERSECURITY
This article is based on a physical round table " We need a quantum step in cybersecurity” organised by Akamai and Pointury on October 20, 2022. We met with top CIO's and CISO's in restaurant Michel in Groot-Bijgaarden to share experiences and insights about cybersecurity.

We need a quantum step in the way our society organises cybersecurity or we will be at the mercy of criminals who use digitalisation to blend traditional activities with cybercrime so as to be grow their lucrative business even faster. To initiate the debate, we invited Eddy Willems, internationally recognised cyber security expert, keynote speaker and author. He is a board member of 3 security industry organisations, EICAR, AVAR and LSEC. Several CERTs, press agencies, print and online publications and broadcasting media, for example CNN, use his advice regularly.
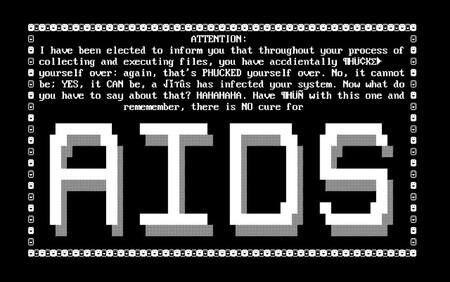
We all have our war stories when it comes to cybersecurity. Eddy’s first war story dates from 1989 when he received a floppy disk, titled "AIDS Information Introductory Diskette". It was created by Dr. Joseph L. Popp, given as a freebee at the WHO conference in 1989 and distributed via PC World Magazine to 20.000 readers. It turned out to be the first ransomware. It caused a lot of damage. Years of AIDS research got lost. Fortunately Eddy was able to decrypt his hard disk in less than 15 minutes. That was the start of his career as cybersecurity expert and resulted in his first media experience.
Now, 33 years later, malware and specifically ransomware is a bigger problem than ever. Some interesting statistics. More than 80% of all attacks are originated from Russia and in more than 60% of the cases companies pay ransom despite strong recommendations to not do so. This makes cybercrime a very lucrative business. Paying ransom might even be funding Russia’s terrorist regime. Only in 90% of the cases when ransomware was paid, a decryption key was obtained. This has been going on for a couple of years and has slightly decreased in 2022. The question rises if this is silence before the storm. Is Russia planning a massive attack at a later date? Eddy does not think so. Yet if they do, it will be in combination with other acts of their hybrid war.
In this context the top tasks for cybersecurity teams are preventing malware, identifying vulnerabilities, preventing phishing attacks and taking corrective and protective measures. Notice that ransomware is a small part of malware. Some cyberattacks in Ukraine and other places were executed to cause damage without a possibility to pay ransomware to recuperate the data. The purpose of the malware attacks was to simply block critical infrastructure.
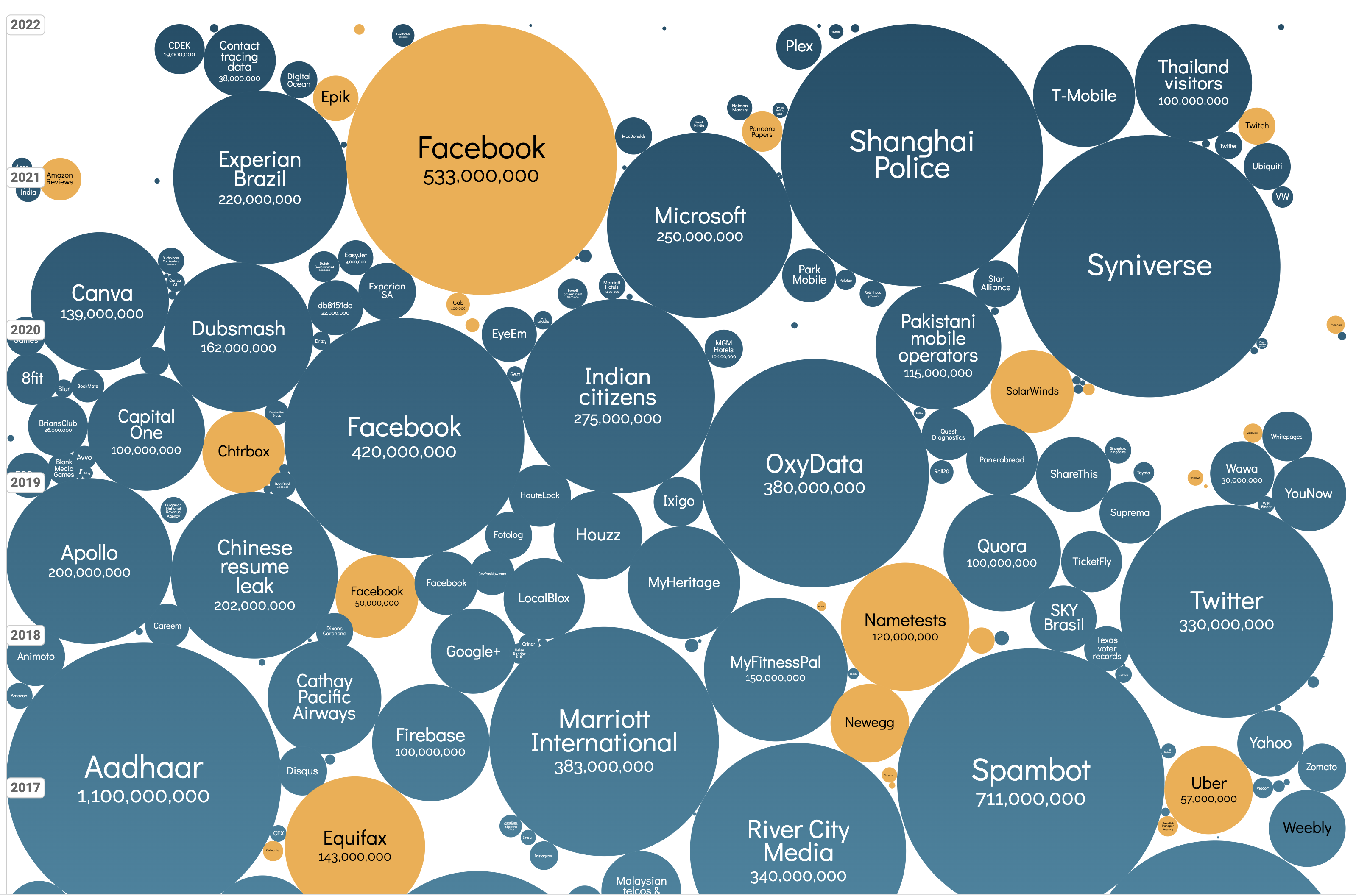
Usually, the start of a malware attacks is unconsciousness behaviour by curious and naïve users. Even the worlds biggest data breaches (see image above) started with a human error. People still click on attachments of phishing emails. Other vulnerabilities causing ransomware infections are poor user practices, maybe due to lack of training, weak passwords and access management, multi-factor authentication fatigue, clickbait, visiting malicious websites, stolen credentials and lack of budget for cybersecurity solutions due to lack of executive buy-in.

In his book “Cyberdanger” Eddy explains that the cybersecurity problem is always a combination of a technology factor (malware) and a human factor (unconscious behaviour).

It is not only the user who can make such mistakes. Also administrators make mistakes. Do all administrators patch their servers? Have all companies implemented multifactor authentication? In the future administrators will also need to check software bill of materials (SBOM) to check what components are included that could be a vulnerability or a strength of the software package.
Mobile devices are easy targets of malware, in particular as most people did not install cybersecurity software on their mobile devices. The situation on iPhones is particular as Apple does not even allow cybersecurity SW to be installed on its devices.
The most common mobile malware attacks include viruses, worms, mobile bots, mobile phishing attacks, ransomware, spyware and Trojans. Some mobile malware combines more than one type of attack. Mobile viruses are adapted for the cellular environment and designed to spread from one vulnerable phone to another.
Conclusion is that humans are the weak link and need to be trained to act in the right way on their PC's and mobile devices. Also administrators need to be trained in cybersecurity. And investments in cybersecurity need to be increased in most organisations.
One last advise from Eddy is to have a memory aid to remind you of the importance of cybersecurity. He kept the floppy disk of the first ransomware attack in a frame in his living room as a reminder.

Akamai powers and protects life online. Leading companies worldwide choose Akamai to build, deliver, and secure their digital experiences — helping billions of people live, work, and play every day. With the world’s most distributed compute platform — from cloud to edge — we make it easy for customers to develop and run applications, while we keep experiences closer to users and threats farther away.
- www.akamai.com
- How to defend against security breaches
- Zero trust security
- Security Solutions
- Guardicore Segmentation
- Contact: Stephen Hartung, Sr Major Account Executive at Akamai Technologies,
shartung@akamai.com


